-
Posts
25 -
Joined
-
Last visited
About iidjscottybxz
- Birthday 09/08/1993
Basic Info
-
Gender
Male
-
Location
England
-
Interests
gaming and networking
-
DumaOS Routers Owned
Netduma R3
XR1000
Gaming
-
Gamer Type
PC Gamer
Console Gamer -
Favourite Genres
Shooters
Racing -
Connection Speed
301-500mbps
Recent Profile Visitors
894 profile views
-
.png) Netduma Frasers reacted to a post in a topic:
Does your WPS work ? (R3 router)
Netduma Frasers reacted to a post in a topic:
Does your WPS work ? (R3 router)
-
.png) Netduma Frasers reacted to a post in a topic:
Does your WPS work ? (R3 router)
Netduma Frasers reacted to a post in a topic:
Does your WPS work ? (R3 router)
-

Does your WPS work ? (R3 router)
iidjscottybxz replied to iidjscottybxz's topic in Community Discussion
some strange reason it don't like my tp-link i have but i have a 2nd router that in Repeater mode that works fine get this message when trying to pair my tp-link these are the new messages i get. (I'm guessing it ant supported with it ?) user.warn com.netdumasoftware.devicemanager: Address family for hostname not supported daemon.err odhcp6c[4038]: Failed to send SOLICIT message to ff02::1:2 (Cannot assign requested address) -

Does your WPS work ? (R3 router)
iidjscottybxz replied to iidjscottybxz's topic in Community Discussion
when i press the wps i get this come on the log about 5 or 6 times daemon.err cli.lua[4135]: [WARNING]: ct c8febeed: time went backwards! -

Does your WPS work ? (R3 router)
iidjscottybxz replied to iidjscottybxz's topic in Community Discussion
yes im on the latest firmware it just don't seem to do anything the wps light don't flash and i don't know if your aware but there seems to something funny with the wireless RGB lights at the front they just don't like up sometimes but when you go into setting and change the Wi-Fi info or bands the lights come on back i might try turn the router back on and off again give that a try -
iidjscottybxz started following Netduma R3 wifi specs ? , Does your WPS work ? (R3 router) and steady ping Netduma R3
-
i have tried pairing my network booster and I've pressed the button on the back for a while and nothing has happened ? cant find in in the router setting ?
-
.png) Netduma Fraser reacted to a post in a topic:
steady ping Netduma R3
Netduma Fraser reacted to a post in a topic:
steady ping Netduma R3
-
yeah i have sorted it out now thanks for the help
-
.png) iidjscottybxz reacted to a post in a topic:
steady ping Netduma R3
iidjscottybxz reacted to a post in a topic:
steady ping Netduma R3
-
im i right in saying this does steady ping only work over wired and not wifi because when i add the devices to steady ping for some reason nothing pops up with anything no severs or info but shows the devices that ive added to steady ping. just wanted to know if i was right or not ?
-
.png) iidjscottybxz reacted to a post in a topic:
Netduma R3 wifi specs ?
iidjscottybxz reacted to a post in a topic:
Netduma R3 wifi specs ?
-
would there be any updates options to the choice of higher channel pick ? and thanks for the info
-
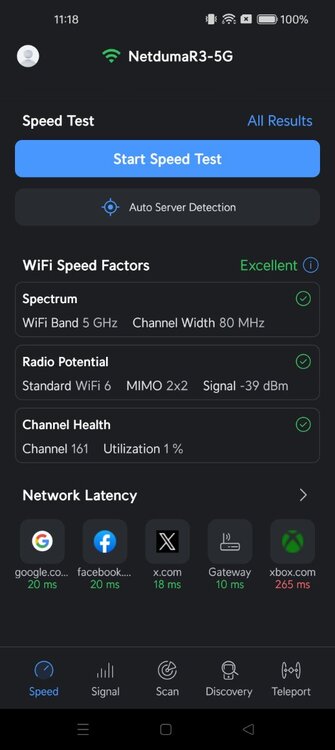
hello this is very strange so i had my 5ghz wifi set to 160mhz on channel 100 was working fine all day today and yesterday i know about DFS channels possbile dected something so changed wifi channel to 80mhz on channel 161 but on there list it only goes up to 128 channels i didnt know it could go higher on channels but the wifi at this channel is very strong and good so ant complaining lol just wanted to know the specs or is the software
-
.png) iidjscottybxz reacted to a post in a topic:
problems with hybrid Vpn
iidjscottybxz reacted to a post in a topic:
problems with hybrid Vpn
-
guess what problem sovled and it was the most random thing ever ! i turned the router on and back on again it dont make sence all that problems but im still on the beta to was going to downgrade again but it seems to be fine now thanks for all your help
-
You on about the system logs ?
-
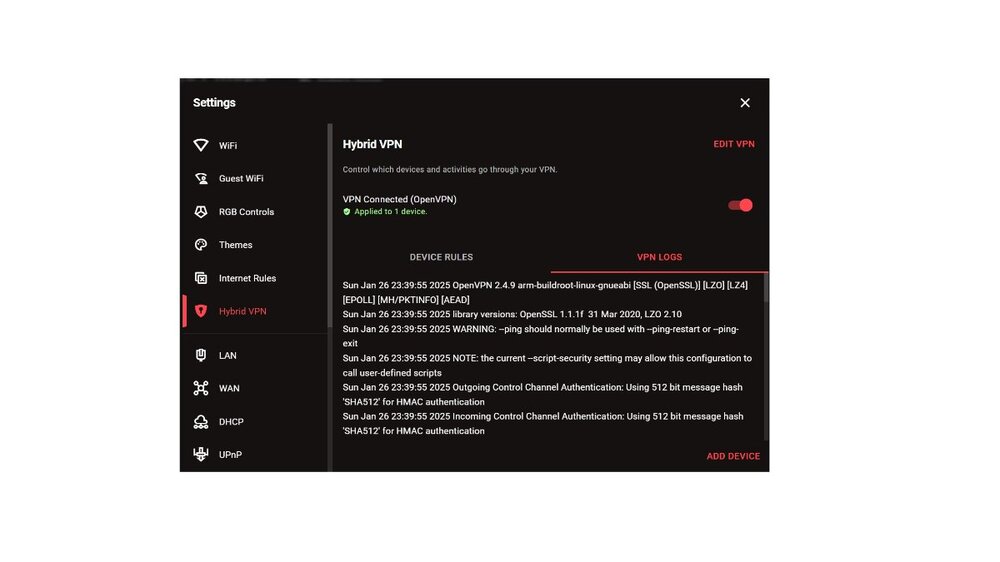
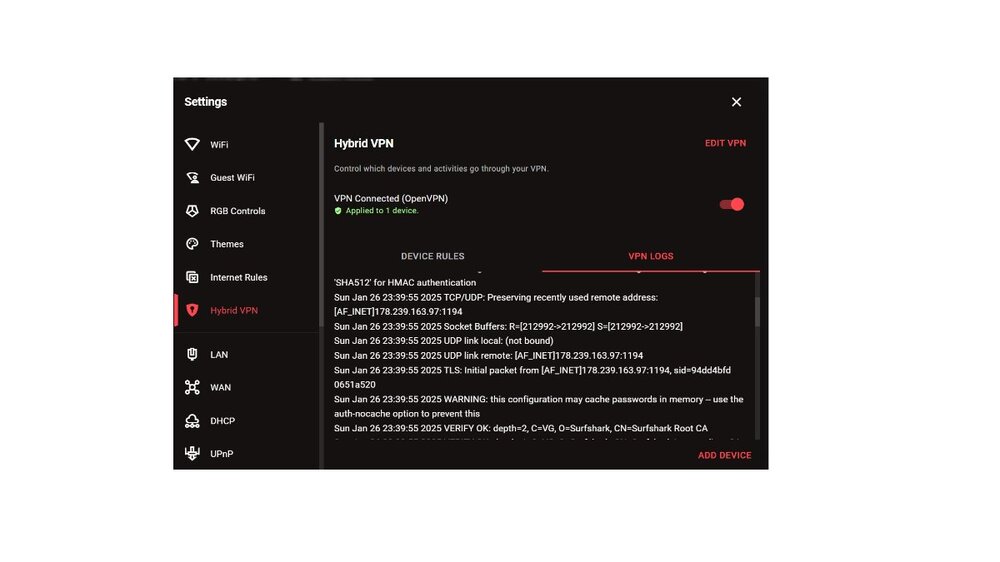
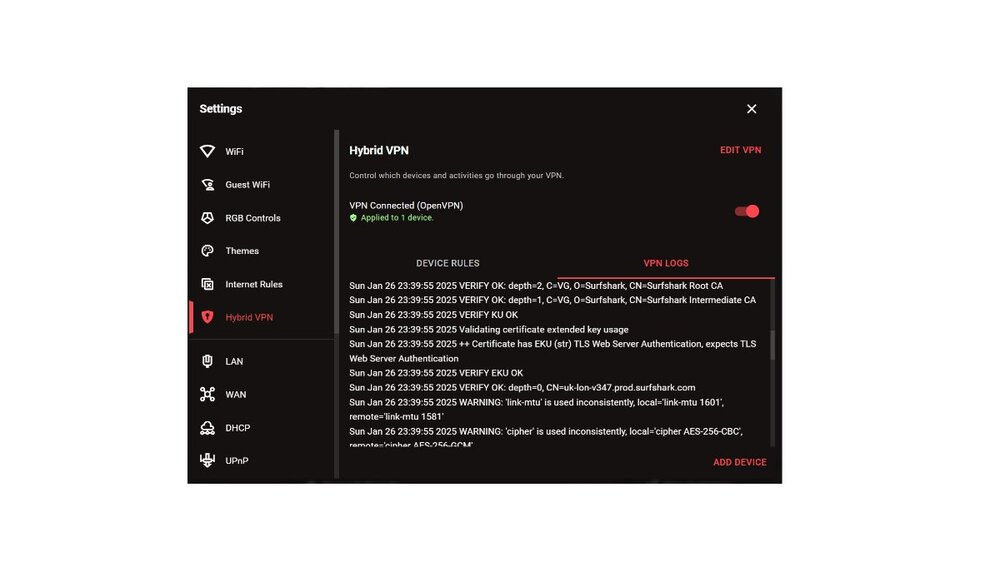
Mon Jan 27 17:55:38 2025 OpenVPN 2.4.9 arm-buildroot-linux-gnueabi [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD] Mon Jan 27 17:55:38 2025 library versions: OpenSSL 1.1.1f 31 Mar 2020, LZO 2.10 Mon Jan 27 17:55:38 2025 WARNING: --ping should normally be used with --ping-restart or --ping-exit Mon Jan 27 17:55:38 2025 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts Mon Jan 27 17:55:38 2025 Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication Mon Jan 27 17:55:38 2025 Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication Mon Jan 27 17:55:38 2025 TCP/UDP: Preserving recently used remote address: [AF_INET]86.106.157.244:1194 Mon Jan 27 17:55:38 2025 Socket Buffers: R=[212992->212992] S=[212992->212992] Mon Jan 27 17:55:38 2025 UDP link local: (not bound) Mon Jan 27 17:55:38 2025 UDP link remote: [AF_INET]86.106.157.244:1194 Mon Jan 27 17:55:38 2025 TLS: Initial packet from [AF_INET]86.106.157.244:1194, sid=e0ed3256 448cb35c Mon Jan 27 17:55:38 2025 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this Mon Jan 27 17:55:38 2025 VERIFY OK: depth=2, C=VG, O=Surfshark, CN=Surfshark Root CA Mon Jan 27 17:55:38 2025 VERIFY OK: depth=1, C=VG, O=Surfshark, CN=Surfshark Intermediate CA Mon Jan 27 17:55:38 2025 VERIFY KU OK Mon Jan 27 17:55:38 2025 Validating certificate extended key usage Mon Jan 27 17:55:38 2025 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication Mon Jan 27 17:55:38 2025 VERIFY EKU OK Mon Jan 27 17:55:38 2025 VERIFY OK: depth=0, CN=uk-lon-v365.prod.surfshark.com Mon Jan 27 17:55:38 2025 WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1601', remote='link-mtu 1581' Mon Jan 27 17:55:38 2025 WARNING: 'cipher' is used inconsistently, local='cipher AES-256-CBC', remote='cipher AES-256-GCM' Mon Jan 27 17:55:38 2025 WARNING: 'auth' is used inconsistently, local='auth SHA512', remote='auth [null-digest]' Mon Jan 27 17:55:38 2025 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, 4096 bit RSA Mon Jan 27 17:55:38 2025 [uk-lon-v365.prod.surfshark.com] Peer Connection Initiated with [AF_INET]86.106.157.244:1194 Mon Jan 27 17:55:39 2025 SENT CONTROL [uk-lon-v365.prod.surfshark.com]: 'PUSH_REQUEST' (status=1) Mon Jan 27 17:55:39 2025 PUSH: Received control message: 'PUSH_REPLY,dhcp-option DNS 162.252.172.57,dhcp-option DNS 149.154.159.92,redirect-gateway def1,sndbuf 524288,rcvbuf 524288,explicit-exit-notify,block-outside-dns,route-gateway 10.8.8.1,topology subnet,ping 60,ping-restart 180,ifconfig 10.8.8.7 255.255.255.0,peer-id 7,cipher AES-256-GCM' Mon Jan 27 17:55:39 2025 Options error: Unrecognized option or missing or extra parameter(s) in [PUSH-OPTIONS]:7: block-outside-dns (2.4.9) Mon Jan 27 17:55:39 2025 OPTIONS IMPORT: timers and/or timeouts modified Mon Jan 27 17:55:39 2025 OPTIONS IMPORT: explicit notify parm(s) modified Mon Jan 27 17:55:39 2025 OPTIONS IMPORT: --sndbuf/--rcvbuf options modified Mon Jan 27 17:55:39 2025 Socket Buffers: R=[212992->425984] S=[212992->425984] Mon Jan 27 17:55:39 2025 OPTIONS IMPORT: --ifconfig/up options modified Mon Jan 27 17:55:39 2025 OPTIONS IMPORT: route options modified Mon Jan 27 17:55:39 2025 OPTIONS IMPORT: route-related options modified Mon Jan 27 17:55:39 2025 OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified Mon Jan 27 17:55:39 2025 OPTIONS IMPORT: peer-id set Mon Jan 27 17:55:39 2025 OPTIONS IMPORT: adjusting link_mtu to 1624 Mon Jan 27 17:55:39 2025 OPTIONS IMPORT: data channel crypto options modified Mon Jan 27 17:55:39 2025 Data Channel: using negotiated cipher 'AES-256-GCM' Mon Jan 27 17:55:39 2025 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key Mon Jan 27 17:55:39 2025 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key Mon Jan 27 17:55:39 2025 TUN/TAP device tun0 opened Mon Jan 27 17:55:39 2025 TUN/TAP TX queue length set to 100 Mon Jan 27 17:55:39 2025 /sbin/ifconfig tun0 10.8.8.7 netmask 255.255.255.0 mtu 1500 broadcast 10.8.8.255 Mon Jan 27 17:55:39 2025 /bin/touch /tmp/lua_7kzYMh tun0 1500 1552 10.8.8.7 255.255.255.0 init Mon Jan 27 17:55:39 2025 Initialization Sequence Completed thats all thats on that again i was thinking of going back of the beta and trying it with out the beta ?
-
nope still the same something is blocking it from going through to the device tried it on the ps5. it cant find a ip address just keeps saying check run a test then it says there is no internet connection even though my pc is on the internet
-
i have not set anything to rules on devices i havent touched anything like that all i have tried to do is put the vpn on and the only thing ive changed in the router setting for the lan is ipv6 on device thats it. i have changed the setting back to normal that hasnt even worked as well so i dont if something in the router is stopping it from working or bug somewhere in the beta i dont know unless its something to do with sufshark maybe the joys of tech
-
Sun Jan 26 23:39:55 2025 OpenVPN 2.4.9 arm-buildroot-linux-gnueabi [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD] Sun Jan 26 23:39:55 2025 library versions: OpenSSL 1.1.1f 31 Mar 2020, LZO 2.10 Sun Jan 26 23:39:55 2025 WARNING: --ping should normally be used with --ping-restart or --ping-exit Sun Jan 26 23:39:55 2025 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts Sun Jan 26 23:39:55 2025 Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication Sun Jan 26 23:39:55 2025 Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication Sun Jan 26 23:39:55 2025 TCP/UDP: Preserving recently used remote address: [AF_INET]178.239.163.97:1194 Sun Jan 26 23:39:55 2025 Socket Buffers: R=[212992->212992] S=[212992->212992] Sun Jan 26 23:39:55 2025 UDP link local: (not bound) Sun Jan 26 23:39:55 2025 UDP link remote: [AF_INET]178.239.163.97:1194 Sun Jan 26 23:39:55 2025 TLS: Initial packet from [AF_INET]178.239.163.97:1194, sid=94dd4bfd 0651a520 Sun Jan 26 23:39:55 2025 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this Sun Jan 26 23:39:55 2025 VERIFY OK: depth=2, C=VG, O=Surfshark, CN=Surfshark Root CA Sun Jan 26 23:39:55 2025 VERIFY OK: depth=1, C=VG, O=Surfshark, CN=Surfshark Intermediate CA Sun Jan 26 23:39:55 2025 VERIFY KU OK Sun Jan 26 23:39:55 2025 Validating certificate extended key usage Sun Jan 26 23:39:55 2025 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication Sun Jan 26 23:39:55 2025 VERIFY EKU OK Sun Jan 26 23:39:55 2025 VERIFY OK: depth=0, CN=uk-lon-v347.prod.surfshark.com Sun Jan 26 23:39:55 2025 WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1601', remote='link-mtu 1581' Sun Jan 26 23:39:55 2025 WARNING: 'cipher' is used inconsistently, local='cipher AES-256-CBC', remote='cipher AES-256-GCM' Sun Jan 26 23:39:55 2025 WARNING: 'auth' is used inconsistently, local='auth SHA512', remote='auth [null-digest]' Sun Jan 26 23:39:55 2025 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, 4096 bit RSA Sun Jan 26 23:39:55 2025 [uk-lon-v347.prod.surfshark.com] Peer Connection Initiated with [AF_INET]178.239.163.97:1194 Sun Jan 26 23:39:56 2025 SENT CONTROL [uk-lon-v347.prod.surfshark.com]: 'PUSH_REQUEST' (status=1) Sun Jan 26 23:39:56 2025 PUSH: Received control message: 'PUSH_REPLY,dhcp-option DNS 162.252.172.57,dhcp-option DNS 149.154.159.92,redirect-gateway def1,sndbuf 524288,rcvbuf 524288,explicit-exit-notify,block-outside-dns,route-gateway 10.8.8.1,topology subnet,ping 60,ping-restart 180,ifconfig 10.8.8.4 255.255.255.0,peer-id 0,cipher AES-256-GCM' Sun Jan 26 23:39:56 2025 Options error: Unrecognized option or missing or extra parameter(s) in [PUSH-OPTIONS]:7: block-outside-dns (2.4.9) Sun Jan 26 23:39:56 2025 OPTIONS IMPORT: timers and/or timeouts modified Sun Jan 26 23:39:56 2025 OPTIONS IMPORT: explicit notify parm(s) modified Sun Jan 26 23:39:56 2025 OPTIONS IMPORT: --sndbuf/--rcvbuf options modified Sun Jan 26 23:39:56 2025 Socket Buffers: R=[212992->425984] S=[212992->425984] Sun Jan 26 23:39:56 2025 OPTIONS IMPORT: --ifconfig/up options modified Sun Jan 26 23:39:56 2025 OPTIONS IMPORT: route options modified Sun Jan 26 23:39:56 2025 OPTIONS IMPORT: route-related options modified Sun Jan 26 23:39:56 2025 OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified Sun Jan 26 23:39:56 2025 OPTIONS IMPORT: peer-id set Sun Jan 26 23:39:56 2025 OPTIONS IMPORT: adjusting link_mtu to 1624 Sun Jan 26 23:39:56 2025 OPTIONS IMPORT: data channel crypto options modified Sun Jan 26 23:39:56 2025 Data Channel: using negotiated cipher 'AES-256-GCM' Sun Jan 26 23:39:56 2025 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key Sun Jan 26 23:39:56 2025 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key Sun Jan 26 23:39:56 2025 TUN/TAP device tun0 opened Sun Jan 26 23:39:57 2025 TUN/TAP TX queue length set to 100 Sun Jan 26 23:39:57 2025 /sbin/ifconfig tun0 10.8.8.4 netmask 255.255.255.0 mtu 1500 broadcast 10.8.8.255 Sun Jan 26 23:39:57 2025 /bin/touch /tmp/lua_chg3wj tun0 1500 1552 10.8.8.4 255.255.255.0 init Sun Jan 26 23:39:57 2025 Initialization Sequence Completed
-
nope still the same i have tried openvpn as well and it not working but i get alot of vpn logs i will send now